PART 1 – Navigating security challenges: The Secure Software Development Lifecycle meets DevOps
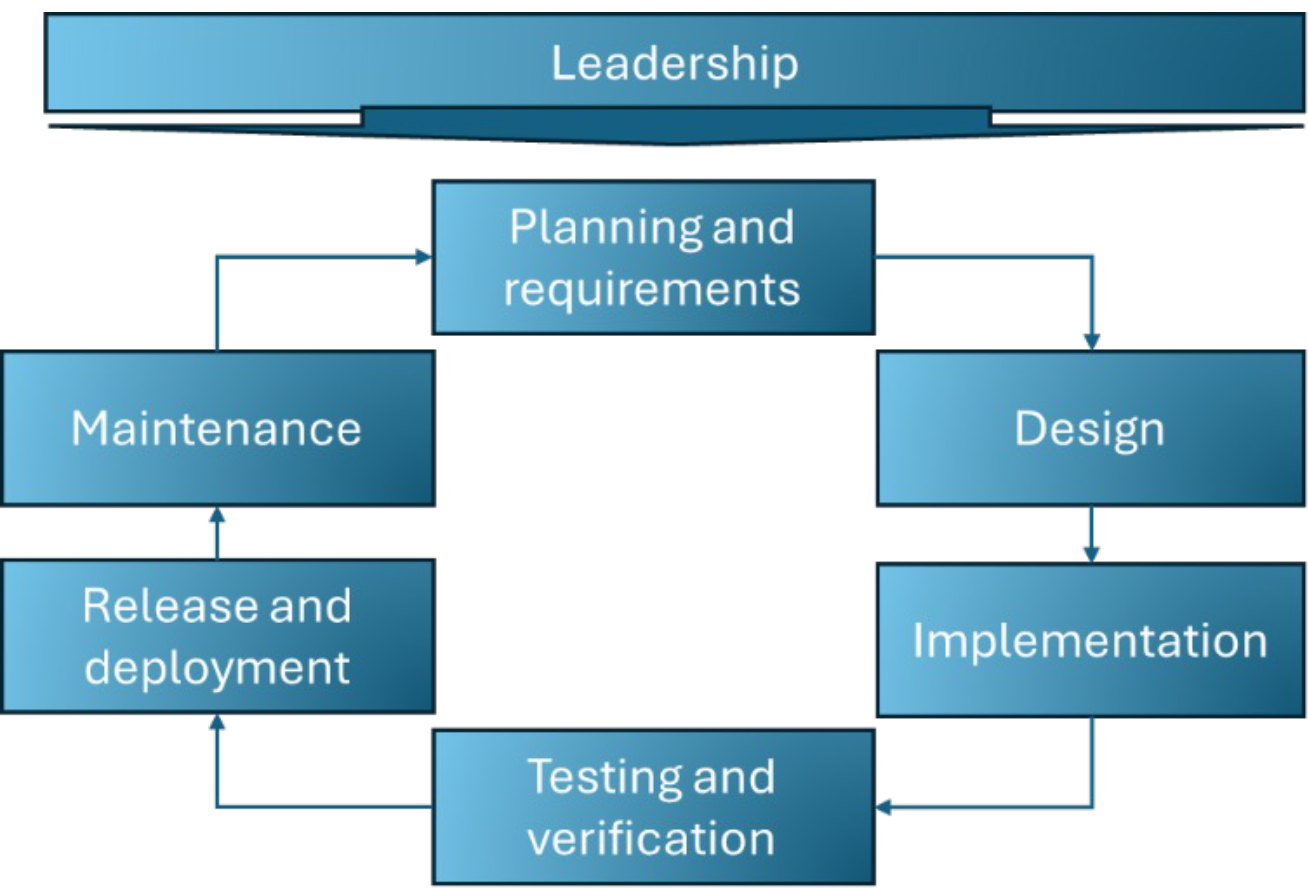
It all starts with leadership
Do you want to keep your services secure and customer data safe while offering users continuous updates and new functionalities? According to metrics available at https://www.cve.org/About/Metrics, almost 29,000 published vulnerabilities were documented in common vulnerabilities and exposure (CVE) records for 2023—and the number keeps growing every year. While it is impossible to achieve absolute security, there are actions companies can embed in their processes to significantly enhance security throughout the development lifecycle even when the pace of development poses challenges.
Motivation and good intentions are not enough. If the management team and organizational leadership aren’t security aware, lack vision in security leadership, or don’t sufficiently support the integration of necessary security improvements across the development cycle, the improvements simply won’t be implemented. In contrast, when a secure development mindset is deeply integrated into an organization’s culture, there is no need for separate security buy-in. Yes, creating such a culture requires investments in money, time, and resources. However, an organization that dedicates itself to secure working practices will eventually attain a level of maturity where security is an integral part of its working standards.
A security-enabled development lifecycle
Ensuring secure processes during each phase of software development ought to be standard practice. But pressures on the pace of development tend to infect the development lifecycle with bad practices, resulting in some or all development phases lacking critical security perspectives and/or appropriate security controls. This may expose the entire development process and its output to potential security breaches and vulnerabilities.
The development lifecycle generally includes the following phases: planning, design, implementation, testing, release/deployment, and maintenance. Individual DevOps models may use slightly different terminology, but regardless of what these phases are called within an organization, the appropriate security measures should be identified, planned for, and embedded into each phase, creating a security lifecycle that mirrors the development lifecycle.
The common anti-pattern is for measures to be implemented for only some—or in the worst cases, none—of the phases of the security lifecycle. Fortunately, there is a movement in the industry to “shift left”: to take security into account earlier in the software development process.
There are prerequisites to be considered before implementing a formal methodology for secure software development. As mentioned, a security vision and leadership support are critical and generally require some level of training for upper management. The scope of the training depends on the organization, but management ought to have an overall idea of what a SSDLC (Secure Software Development Life Cycle) means, what it involves, and most importantly, why it is necessary.
A familiarity with key terms used within the selected security methodology is also useful. Training and awareness are fundamental building blocks for establishing and strengthening the security culture of an organization. The scope of such training and training-related metrics are a subject for a different post.
In Part 2 we’ll delve into phases of secure development lifecycle …
Jari Mannonen is working as the Head of Cyber Security Development at Piisku. He has over 20 years of consultancy experience in business-critical information technology and application architecture, with a focus on cybersecurity.
In this article, we have used AI-generated images.